The internals workings of the platform. This goes in detail regarding the underlying technology and more!
CircuitsArchitecture
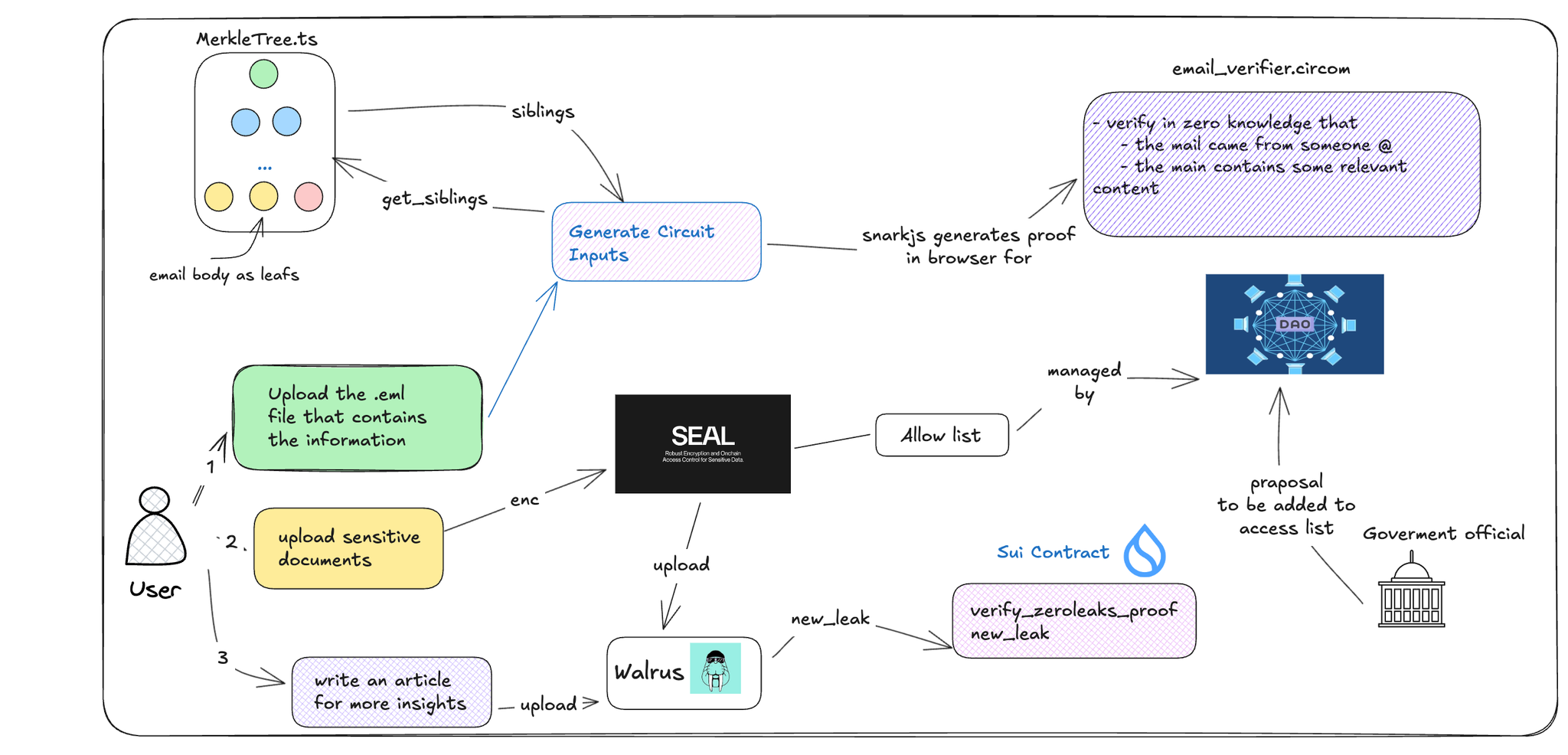
User Flow (Steps 1 → 2 → 3)
- Upload the
.emlfile
The user uploads an email (
.eml) that contains incriminating or whistleblowing content.- Upload Sensitive Documents
The user also uploads supporting documents (e.g., PDFs, images, reports) which are encrypted using SEAL, your on-chain encryption system.
- Write an Article (Optional)
The user may write an explanatory article giving insights or context to the documents and email. This can be used for publishing or further evaluation.
More details here
Merkle Tree Construction
- The email body is split into leaves in
MerkleTree.ts.
- You then compute the Merkle siblings of the content and extract them using
get_siblings.
- This prepares the inclusion proof that will be used in the ZK circuit. More detail here
Document Encryption & Access Control
- The uploaded documents are encrypted using SEAL, a secure on-chain encryption + access-control system.
- These encrypted documents are stored on Walrus, a secure storage layer.
- The ZK proof (generated earlier) is uploaded along with metadata to Walrus via a
new_leak.
Governance & Access List
- DAO Governance manages the allow-list for accessing leaked documents.
- The
Allow listin SEAL ensures only legislative authorities
- Government officials (or other high-authority roles) may propose themselves to be added to the access list via on-chain DAO governance.